At PeerDB, we are building a fast and a cost-effective way to replicate data from Postgres to Data Warehouses, Queues and Storage. This blog post talks about how PeerDB accesses Postgres Databases securely via SSH Tunneling and moves data to any of its supported targets.
What is SSH Tunneling?
SSH (Secure Shell) Tunneling is a method for connecting to services over unsecured networks, creating a protected pathway for data to travel and encrypting the information exchanged.
A tunnel is created via a SSH Bastion (or Jump Box) to an application (usually) inaccessible from the outside world:
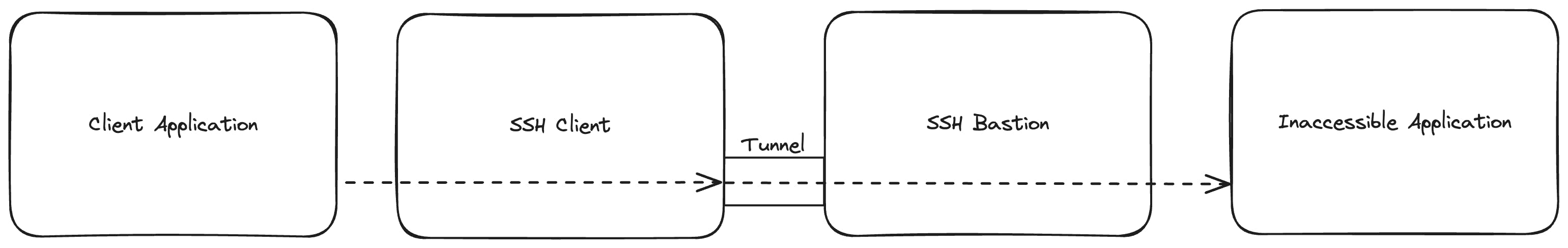
The client application (which can be on the same host as the SSH Client) can now access the previously inaccessible application via the established tunnel.
Why Use SSH Tunneling?
PeerDB uses SSH Tunneling to securely connect and move data from your Protected Postgres Database(s) to a variety of targets in a cost-effective manner:
Accessing Protected Resources Securely
Resources such as Databases are usually not made accessible from outside the VPC of the hosted cloud or the on-premises server. SSH Tunneling ensures a secure pathway for data transmission to and from the protected resource.
Cost-Effective Data Integrity
Investing in a secure data access solution is a strategic move for any business. SSH Tunneling minimizes the need for complex infrastructure, offering a cost-effective strategy to ensure data integrity without inflating operational costs.
It just requires a lightweight SSH Bastion (VM or EC2 instance) and a couple of firewall rules to get going.
Securing Postgres Replication with PeerDB's SSH Tunneling
Let's say we have a Postgres Database in the cloud (say RDS) which is inaccessible via the public internet and is only accessible via specific resources inside its VPC.
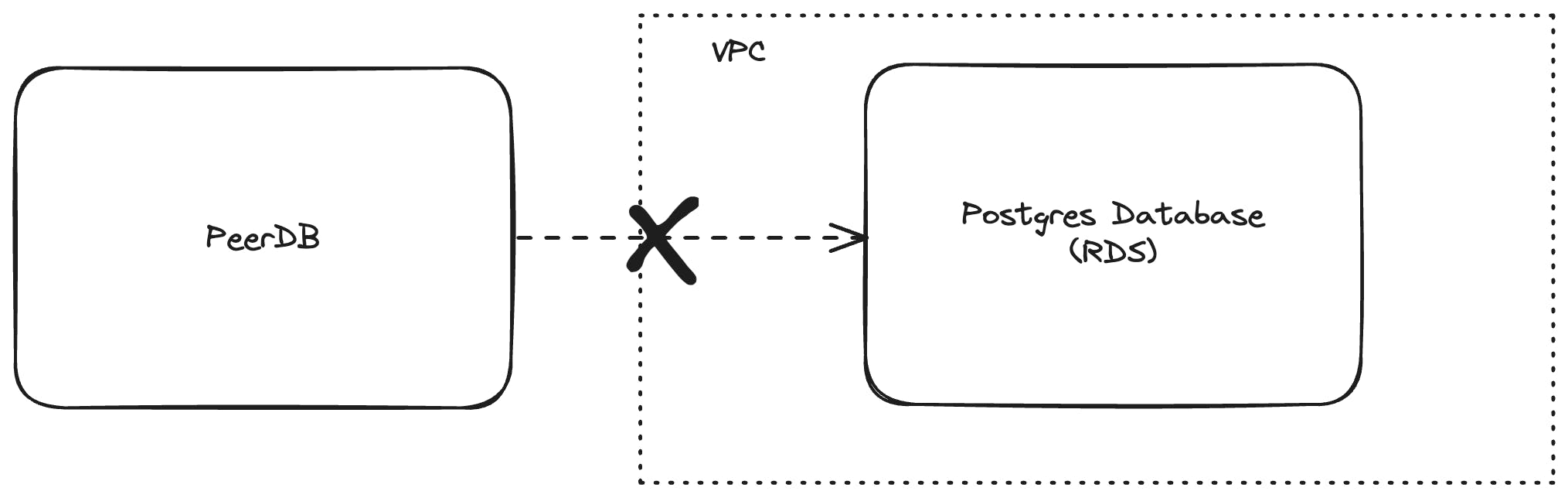
How can you connect PeerDB to such a Postgres DB?
The Setup
You only need 2 things to set up the tunnel:
A Bastion or JumpBox (an EC2 Instance)
Firewall rules for
Bastion to be able to access the RDS (Security Group - Inbound Rule)
PeerDB to be able to connect to the Bastion (Security Group - Inbound Rule)
The setup should look something similar to this:

Nothing more is required as PeerDB takes care of the rest.
PeerDB to the Rescue
It just takes a few seconds to connect to Postgres via an SSH Tunnel in PeerDB:

This is how the end result looks like:
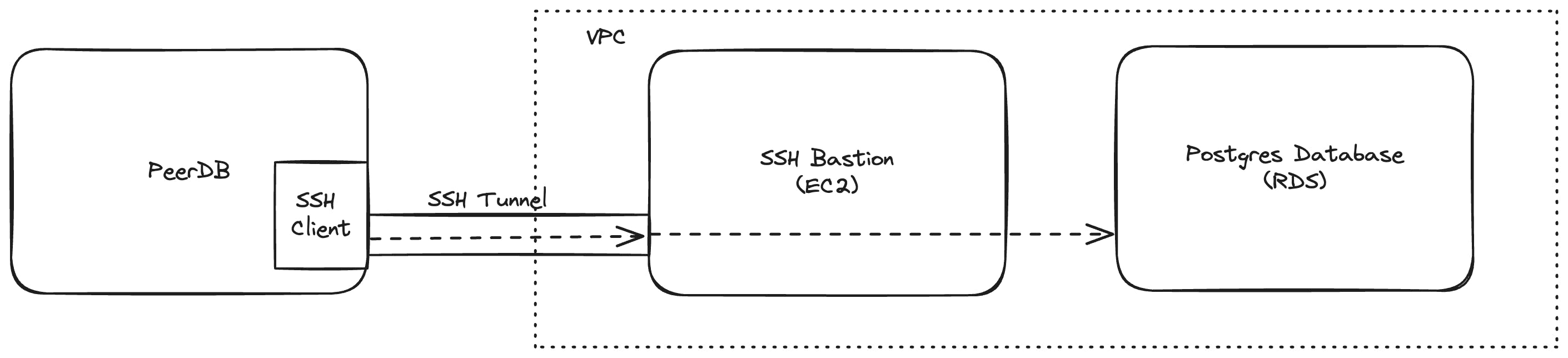
We've integrated SSH Tunneling into the heart of the PeerDB, so now anyone can simply configure the tunnel with minimal extra configuration (like the Bastion information), with the PeerDB server automatically setting it up and using it to connect to the protected Postgres database.
Conclusion
Thank you for reading our blog! If you want to try out this new feature SSH Tunneling to securely connect and replicate data from your Postgres Database to Data Warehouses:
Try out the Free Trial of our fully managed offering. OR
Visit our GitHub repository to Get Started.

